University of Wolverhampton's Data Breach Incident Management Policy and Guidance
The University of Wolverhampton (“the University”) is committed to compliance with Data Protection Legislation. This Policy has been approved by the University’s Board of Governors. It sets out the University’s requirements for dealing with personal data breaches.
This policy has been reviewed in accordance with requirements set out within the UK General Data Protection Regulations (UK GDPR) and the Data Protection Act 2018 (DPA).
This Policy is intended to supplement the University Data Protection and other information security policies and has been developed with the aim of aiding the understanding of the University’s obligations in the event of a data security breach.
The UK GDPR and the DPA require that personal data is processed fairly, lawfully and not in ways which would have unjustified adverse effects on the individuals concerned.
The Data Breach Incident Management Policy and Guidance applies to all employees of the University including contractors and those who are within a probationary period. The policy applies to students doing research on behalf of the University, using personal data controlled by the University.
The policy does not apply to students conducting research for the purpose of their own studies, using data which is not controlled by the University. This is because students processing personal data to conduct research for their studies is outside the UK GDPR’s scope as it is considered a domestic purpose. Personal data processed in the course of a purely personal activity, with no connection to a professional or commercial activity, is outside the UK GDPR’s scope.
University employees who fail to adhere to the terms of this policy may be subject to disciplinary action, up to and including dismissal.
This policy applies to all methods of processing of personal information, including research, on any device, whether University or personally owned, which is used for University purposes, whether, on a regular or an ad-hoc basis.
Data Controller: the person or organisation that determines when, why and how to process personal data. It is responsible for establishing practices and policies in accordance with the UK GDPR. The University is the Data Controller of all personal data relating to it and used delivering education and training, conducting research and all other purposes connected with it including business purposes.
Data Protection Officer (DPO): the person appointed as such under the UK GDPR and in accordance with its requirements. A DPO is responsible for advising the University (including its employees) on their obligations under Data Protection Law, for monitoring compliance with data protection law, as well as with the University’s polices, providing advice, cooperating with the ICO and acting as a point of contact with the ICO.
Data Subject: a living, identified or identifiable individual about whom we hold personal data.
Information Asset Owner: Staff across the university have been assigned the role of Information Asset Owner (IAO) by their director or Dean. These staff work with the Data Protection Officer and Information Governance Team in ensuring compliance with the Data Protection Act 2018 for their directorate/team and faculty.
Information Asset Custodian: Staff across the university have been assigned the role of Information Asset Custodian (IAC) by their director or Dean. These staff work with and assist the IAO in ensuring compliance with the Data Protection Act 2018 for their directorate/team and faculty.
Personal Data: any information identifying a data subject or information relating to a data subject that we can identify (directly or indirectly) from that data alone or in combination with other identifiers we possess or can reasonably access. Personal data includes sensitive personal data and pseudonymised personal data but excludes anonymous data or data that has had the identity of an individual permanently removed.
Personal Data can include the following:
a. Name and address (postal and email)
b. Date of birth
c. Statement of fact
d. Any expression or opinion communicated about an individual
e. Minutes of meetings, reports
f. Emails, file notes, handwritten notes, sticky notes
g. CCTV footage if an individual can be identified by the footage
h. Employment and student applications
i. Spreadsheets and/or databases with any list of people set up by code or student/staff number
j. Employment or education history
k. Online identifier, IP address
Personal Data Breach: any breach of security resulting in the accidental or unlawful destruction, loss, alteration, unauthorised disclosure of, or unauthorised access to, personal data, where that breach results in a risk to the data subject. It can be an act or omission.
Processing or Process: any activity that involves the use of personal data. It includes obtaining, recording or holding the data, or carrying out any operation or set of operations on the data including organising, amending, retrieving, using, disclosing, erasing or destroying it. Processing also includes transmitting or transferring Personal Data to third parties. In brief, it is anything that can be done to personal data from its creation to its destruction, including both creation and destruction.
Special category data: any information identifying a data subject or information relating to a data subject that we can identify (directly or indirectly) from that data alone, or in combination with other identifiers we possess or can reasonably access about living individuals:
a. Race or ethnicity
b. Religious or philosophical beliefs
c. Political opinions
d. Membership of a trade union
e. Genetic data
f. Biometric data
g. Health data
h. Sex life
i. Sexual orientation
Managers
Are responsible for supporting employees in identifying whether a personal data breach has occurred, ensuring the employee reports it, or reports it on their behalf if the employee is unable to. The reporting procedure can be found in section 7.2.
They are also responsible for ensuring any mitigative measures advised by the Information Governance Team (the IG Team) are put in place.
Employees
Are responsible for identifying whether a personal data breach has occurred and if it has occurred, reporting it immediately after they are discovered. The reporting procedure can be found in section 7.2.
They are also responsible for ensuring any mitigative measures advised by the IG Team are put in place. This includes any mitigative actions advised resulting from a breach caused by a student conducting research for the University.
Students conducting research for the University
Are responsible for identifying whether a personal data breach has occurred and if it has occurred, reporting it immediately after they are discovered. The reporting procedure can be found in section 7.2.
Information Asset Owners
Are responsible for liaising with the IG Team and the reporting employee when a personal data breach is reported. When necessary, they are also responsible for supporting employees in identifying whether a personal data breach has occurred, ensuring the employee reports it, or reports it on their behalf if the employee is unable to. The reporting procedure can be found in section 7.2.
They are also responsible for ensuring any mitigative measures advised by the IG Team are put in place.
Information Governance Team
Are responsible for liaising with employees, IAO’s, managers and any other employees necessary to resolve and risk assess personal data breaches. The IG Team should advise of any mitigative measures necessary to reduce the risk of the personal data breach and reduce the likelihood of them occurring in the future.
A personal data breach can be broadly defined as a security incident that has affected the confidentiality, integrity or availability of personal data. There will be a personal data breach whenever any personal data is accidentally or deliberately lost, destroyed, corrupted or disclosed; if someone accesses the data or passes it on without proper authorisation; or if the data is made unavailable and this unavailability has a significant negative effect on individuals. Breaches can be a result of both accidental and deliberate causes, including:
- Access by an unauthorised third party.
- Deliberate or accidental action (or inaction) by a controller or processor.
- Sending personal data to an incorrect recipient.
- Unencrypted computing devices containing personal data being lost or stolen.
- Alteration of personal data without permission.
- Loss of availability of personal data.
A personal data breach can occur for a number of reasons, such as:
- Loss or theft of data or equipment on which data is stored.
- Inappropriate access controls allowing unauthorised use.
- Equipment failure.
- Human error.
- Unforeseen circumstances such as fire or flood.
- Hacking attack.
- Offences where information is obtained by deceiving the holder of the information, the University.
- Physical security breach e.g. unlocked buildings, filing cabinets.
A near miss is where, but for human or artificial intelligence intervention, a data breach would have occurred. The University can learn valuable lessons from near misses and so staff and students are encouraged to report these as well as any actual breaches.
Special category data is especially sensitive and the exposure of it could significantly impact the rights and freedoms of data subjects and potentially be used against them for discrimination.
Members of staff and students at the University, who access, hold or process personal or special category data for the purposes of University business must take appropriate steps to minimise the risk of accidental loss, destruction of, or damage to personal data occurs.
Containment and recovery
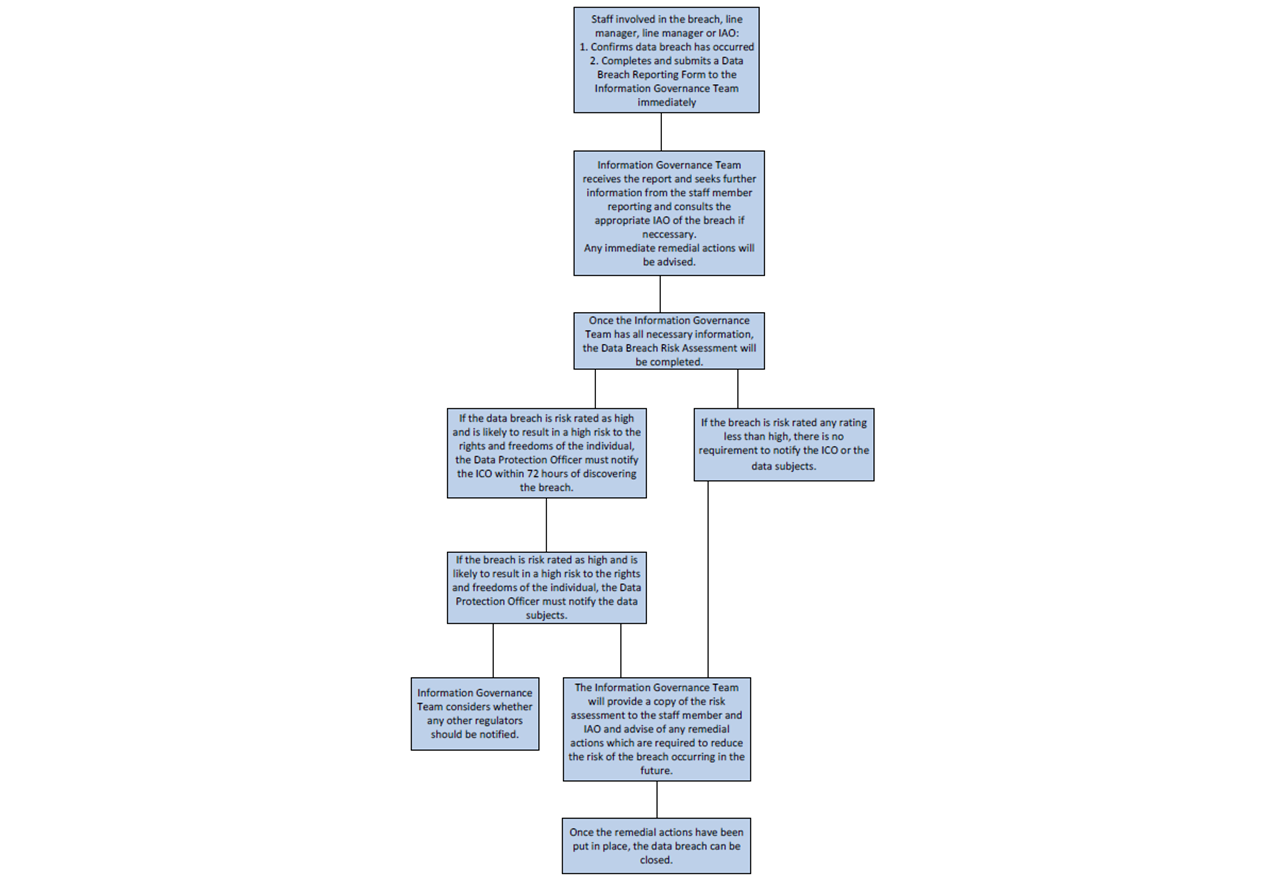
Personal data breaches should be contained and responded to immediately upon discovery by the member of staff or student involved in the breach and their line manager (if available). Steps should be taken to identify measures required to contain or limit potential damage and recover from the incident. The IG Team will advise of the most appropriate measures to be put in place, depending on the circumstances of the breach.
Staff and students should not attempt to contact the data subject/s whose data has been compromised because of the personal data breach, unless they have been advised to do this by the IG Team.
If the breach has occurred because of an email being sent to the incorrect recipient, the staff member or student should attempt an email recall immediately. Instructions on how to perform an email recall can be found at Appendix 1.
All data breaches must be reported to the Data Protection Team via the online Data Breach Incident Reporting Form, found on the Internal Data Protection Webpage by staff member or their line manager, or the student or their supervising staff member immediately after discovery (weekends and Bank Holidays excluded). If the personal data breach involves an IT Security incident and it is possible that University IT systems have been breached or compromised, Digital Services should be alerted by contacting itsupport@wlv.ac.uk.
Assessing the Risk
Some personal data breaches may not lead to risks beyond possible inconvenience to those who need the data to undertake their role (e.g., a laptop is irreparably damaged, but its files were backed up and can be recovered). Following immediate containment, the IG Team must assess the risks which may be associated with the breach.
In undertaking the risk assessment, the IG Team will have regard to the guidelines published by Information Commissioner’s Office (ICO) and the Article 29 Working Group (or any successor body). The IG Team uses a risk assessment questionnaire and will also consider the following when making their assessment:
- The type of personal data involved.
- The sensitivity of the personal data.
- If the data has been lost or stolen, whether it has been protected by encrypted devices or software
- What has happened to the data, such as the possibility that it may be used to cause harm to the data subjects/s
- Whether there are wider consequences to the breach.
- Whether any actions have been taken during the breach that contravene the policies, procedures and training in place.
Notification of Data Breaches
Pursuant to the UK GDPR, a data controller is obliged to inform the ICO if the data breach is likely to result in a high risk to the rights and freedoms of the data subjects affected, within 72 hours of establishing that a breach has occurred. The IG Team will decide on whether to notify the ICO while completing the risk assessment. The IG Team will also identify whether any other appropriate regulatory authority should be notified.
Pursuant to the UK GDPR, where there is a high risk to the rights and freedoms of the affected data subjects’ consideration should also be given to whether or not to notify them. If it is decided that notification is necessary, this should be done without undue delay. The IG Team will make the determination in parallel with that for notification to the ICO.
Serious high-risk breaches may require a ‘media message’ to be communicated to individuals concerned and the public at large, dependent on the seriousness and extent of the breach, which should be considered and implemented where appropriate. The IG Team will coordinate this with the Corporate Communications Team if necessary.
Evaluation and Response
The IG Team will keep a register of all data breaches reported. The IG Team will also keep a register of all risk assessments, in which the IG Team will also record their decisions on notifications and remedial action.
The completed risk assessment will be provided to the employee and the IAO. This will include any remedial actions which require implementation by the employee, their line manager or the IAO.
Where a breach is caused by systematic and ongoing problems, merely containing the breach and continuing ‘business as usual’ will not be deemed acceptable. Areas requiring improvement for the purposes of preventing a re-occurrence should be identified by the line manager and the IAO, with the process owner if appropriate and Policies and Procedures should be updated or implemented, as appropriate.
Relevant lessons learnt will be fed back to the service and/or school to implement the required changes and or guidance or training. Lessons learnt will be fed back to the individual and team where the breach took place, as well as to the Information and Data Quality Committee and IOA group. Where serious incidents and or breaches have occurred, lessons may be shared more widely. Any risks signed off and associated actions will be maintained in a risk log by the IG Team and made available to Information and Data Quality Committee.
Flowchart
A flowchart summarising this process can be found at Appendix 2.
Training is equipping staff, students (and others where appropriate) with the relevant skills required for/with this policy and procedure. Training relating to this policy and briefing will be made available in a range of formats according to the needs of the trainee and different groups of staff, students and others.
All staff undertake annual mandatory data protection training and IAOs/IACs undertake advanced data protection training annually. Faculty and other staff which require access to Business Objects and Tableau reports, are also required to undertake this advanced training.
There are no exceptions to this policy.
This Policy was approved by the University’s Board of Governors on 28 June 2023. The University may change this Policy at any time, and where appropriate. Where a policy is not due for review, but is found to require updating, it will remain published, unless the reasons for review render it obsolete.
You may find it useful to refer to the Data Protection Policy when reading this policy.
The Data Protection Policy can be found on the University Policy Hub at the following link: WLV Policies - University of Wolverhampton.
For general queries, please contact the University Data Protection Officer by email or phone.
Email: dataprotection@wlv.ac.uk
For general queries, please contact the University Corporate Compliance Team via email: compliance@wlv.ac.uk.
| Version | Approval Date | Review Date | Author/Owner | Approved By |
|---|---|---|---|---|
| 1.3 |
16 May 2023
28 June 2023 |
16 May 2026
28 June 2026 |
Data Protection Officer/Chief Compliance Officer |
University Executive Board Board of Governors |
If you have sent an email to the wrong person, you must recall the message immediately.
- Select the Sent Items folder.
- Select or double-click the message so it opens in another window.
- Select File > Info.
- Select Message Resend and Recall > Recall This Message - then select one of the two options.
- Select the Tell me if recall succeeds or fails for each recipient check box.
- Select OK.
Guidance on reducing the risk of data breaches occurring.
The below measures should be considered and put in place to reduce the likelihood of a personal data breach occurring.
Sending emails
- Take time when sending emails and ALWAYS double-check the recipients email address before sending the email.
- Add a delay to all emails up to five minutes, so emails can be cancelled if the error is realised in time.
- Password protect any attachments which contain personal data. Documents containing special category data and financial data MUST be password protected at all times.
- Use Egress to send emails/documents containing sensitive data as access can be revoked and an audit trail is created.
- Avoid using personal student or staff email addresses.
- Use Teams to communicate or share documents where possible and appropriate. Teams messages can be deleted if sent in error and access from documents sent in error can be removed.
Document Storage and Sharing
- Use OneDrive and SharePoint for document storage where possible rather than shared files.
- Documents and entire files can be shared via OneDrive and SharePoint by sharing links with people or granting them access. This will help keep one version of a document with personal data and avoid lots of different versions being stored on different devices and in different locations.
- If links or access are providing to incorrect recipients, access can easily and quickly be revoked.
Using Canvas, Panopto and other VLE’s
- Share assignment/exam feedback on e:vision or Canvas if possible.
- Regularly review Canvas guidance to refresh knowledge on set up processes.
- Double check classes and other set-ups are done correctly.
- Review settings before sending notifications.
- Double check links are correct before sending them to students.
Other
- Always close windows containing/showing personal data not applicable or in use when you are presenting your screen to a class or other staff.
- Only use USB sticks when necessary. Always encrypt USB sticks when they contain personal data.
- Always keep filing cabinets containing personal data locked and keep the key in a different location.
- Always clear your desk when leaving it unattended.
- If you have an office, lock the door when leaving the room.
Working from home
Sharing Information
When working from home you should not:
- Share log in information with members of the household.
- Share your encryption key with members of the household.
- Share student or staff personal information with members of the household.
Hard Copies
- Use only hard copy documents containing personal information when necessary.
- Store in a locked and safe place when not in use and use a crosscut shredder to destroy.
- If printing or scanning, remove hard copies containing personal information as soon as you have finished.
When using your own device
- Before others use the device, log out.
- Documents containing personal information should not be stored on the device hard drive including:
- Web hosted platforms on the device
- Other platforms such as Outlook.
Other
- Log out or lock your device, if you are away from it.
- When discussing personal data, use a private space.
- After installing updates, make sure to
- Ensure your home router is not using the default administrator password and IP address.


/prod01/wlvacuk/media/departments/digital-content-and-communications/images-18-19/iStock-163641275.jpg)
/prod01/wlvacuk/media/departments/digital-content-and-communications/images-2024/250630-SciFest-1-group-photo-resized-800x450.png)
/prod01/wlvacuk/media/departments/digital-content-and-communications/images-18-19/210818-Iza-and-Mattia-Resized.jpg)
/prod01/wlvacuk/media/departments/digital-content-and-communications/images/Maria-Serria-(teaser-image).jpg)
/prod01/wlvacuk/media/departments/digital-content-and-communications/images-2024/241014-Cyber4ME-Project-Resized.jpg)
/prod01/wlvacuk/media/departments/digital-content-and-communications/images-18-19/210705-bric_LAND_ATTIC_v2_resized.jpg)